BlueKeep Vulnerability: This year's WannaCry - and worth your time
In May, Microsoft issued a rare critical vulnerability notice, even going so far as to release updates for legacy platforms such as Windows XP and Windows 2003, despite them being outside of extended support. The vulnerability, nicknamed 'BlueKeep' is a scary one - essentially allowing Remote Desktop Protocol to be leveraged as an attack vector, and an entire machine to become compromised. That said, it was viewed as somewhat of an academic, albeit alarming, exploit - until the working exploits began surfacing.
As of June, 2019 - as many as 40% of affected machines worldwide were potentially still exposed to this vulnerability - and the risk is not just academic. Just this morning, security firm Sophos announced a working proof of concept showing yet another method for capitalizing upon the BlueKeep exploit.
The slightly silver lining here is that newer versions of Windows aren't affected - anything after Windows 7 or Server 2008 is not at risk - but that bad news is that most organizations still have these older platforms knocking around their network.
So what should you do?
Simply put, the action you should be taking here is patching this critical vulnerability - and ensuring that you have not neglected any machines still exposed to this vulnerability.
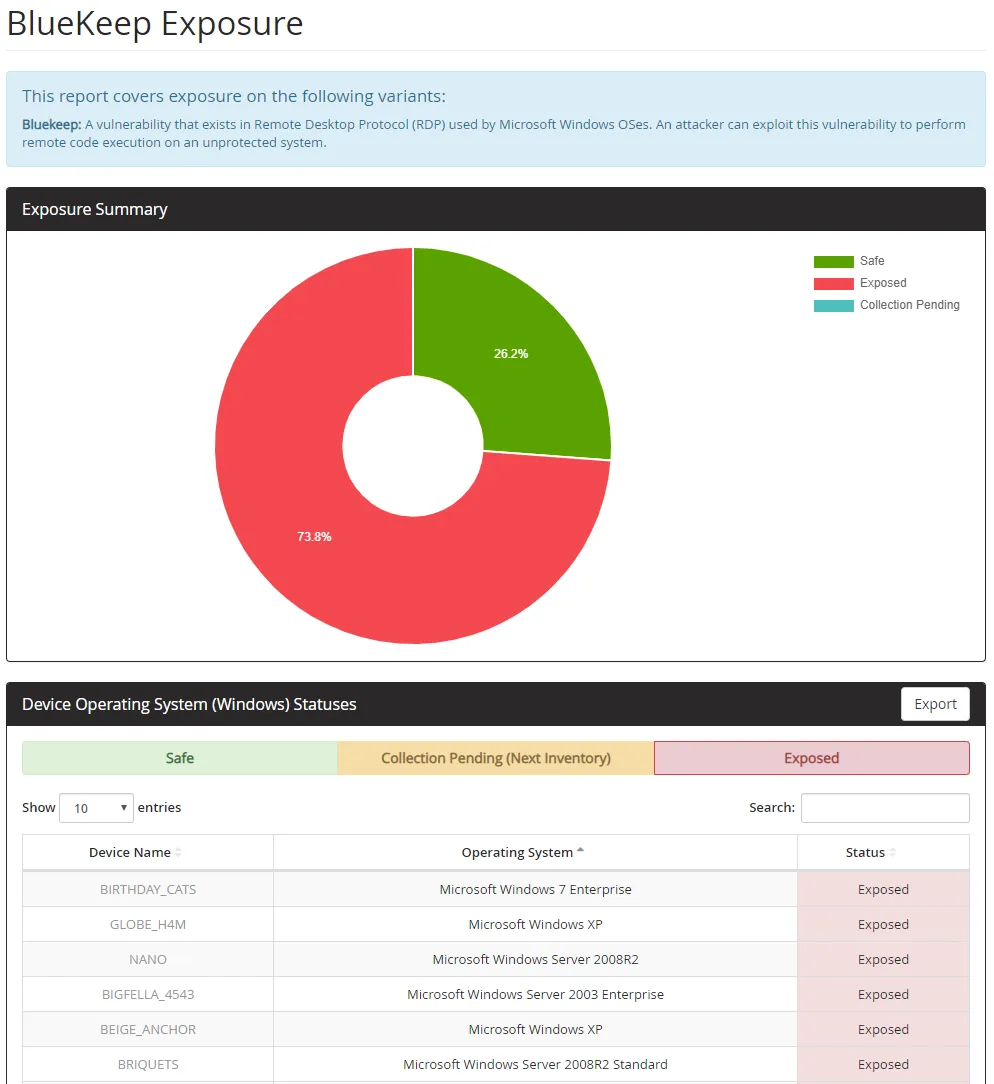
The quickest path to determining your exposure is ensuring the proper hotfixes have been applied. Block 64 has released a BlueKeep-focused report - if you're currently one of our customers, it has been added to our suite of security reports and you can gauge your exposure immediately.
In addition to patching, blocking RDP (port 3389) in any external-facing cases will prevent attacks from outside the network - and of course, while RDP has many legitimate uses, if you are not making use of it in your organization, disabling it via Group Policy is another way to reduce your attack surface.
If you'd like help taking a look for yourself, or gathering the data that will allow you to quickly and completely assess whether this affects you - simply let us know.
For more information about Block 64 or to reach out, please visit us athttp://www.block64.com.