Stop paying for technology you don’t use
Block 64 helps IT teams cut up to 30% of wasted SaaS, cloud, software and hardware spend. No consultants, spreadsheets, or six-figure tools required.
Trusted by Leading Solutions Providers
Most of your IT stack is in the dark
56% of your IT budget is spent on SaaS, cloud, software and hardware, and your team is relying on spreadsheets and siloed tools to manage it.
No wonder your IT spend keeps rising while security gaps and compliance risks remain.
Poor IT visibility
costs more than you think
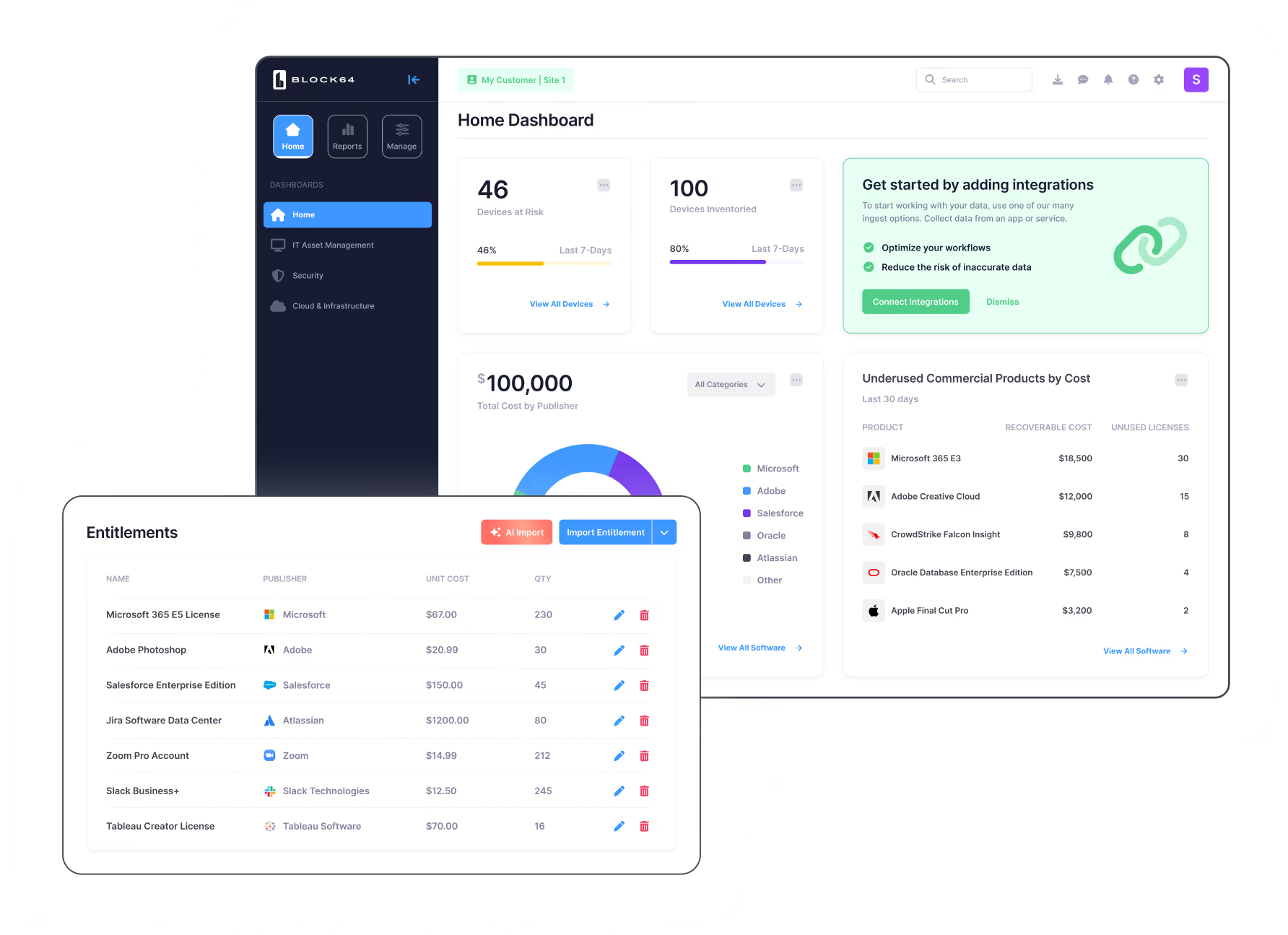
Finally, one platform that delivers total visibility
Block 64 is the only unified platform that provides lean IT teams a consolidated asset inventory, including all hardware and software installed from data center to desktop, on premise and in the cloud.
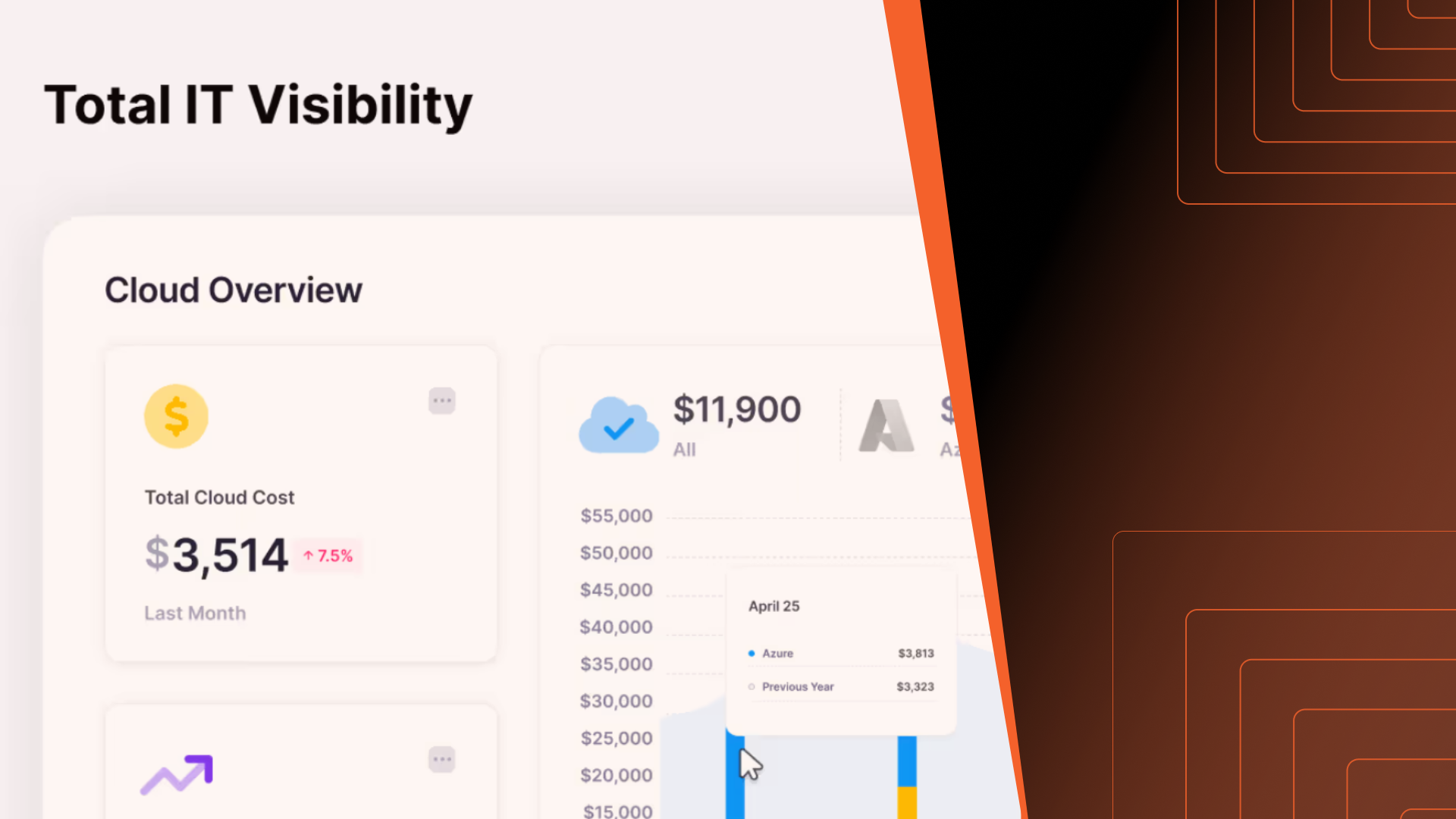
See everything,
waste nothing
Block 64 gives you the information you need to make IT decisions with confidence.
Get started in
three simple steps
Step 1 – Discover
Deploy and configure data collection technologies, ensuring thorough and complete discovery in all types of environments; concentrated, distributed, low connectivity or dark-to-web, our flexible solution combines agentless, agent and vendor API services to get it all.
Step 2 - Analyze
Our platform automatically categorizes assets, identifies usage patterns, flags security risks, and uncovers cost-saving opportunities in one unified dashboard. From data to insights in your first session.
Step 3 - Optimize
Use Block 64's recommendations to eliminate waste, reduce security risks, and streamline compliance - with clear ROI reports you can share with leadership. Start measuring value in days, not quarters.
That’s it – you’re in control!
No hidden steps. No waiting games. With your IT estate mapped, analysed, and optimised, you’re ready to act with confidence - backed by real data, not guesswork.
Easy to deploy
and easy to own
.png)
What makes
Block 64 different
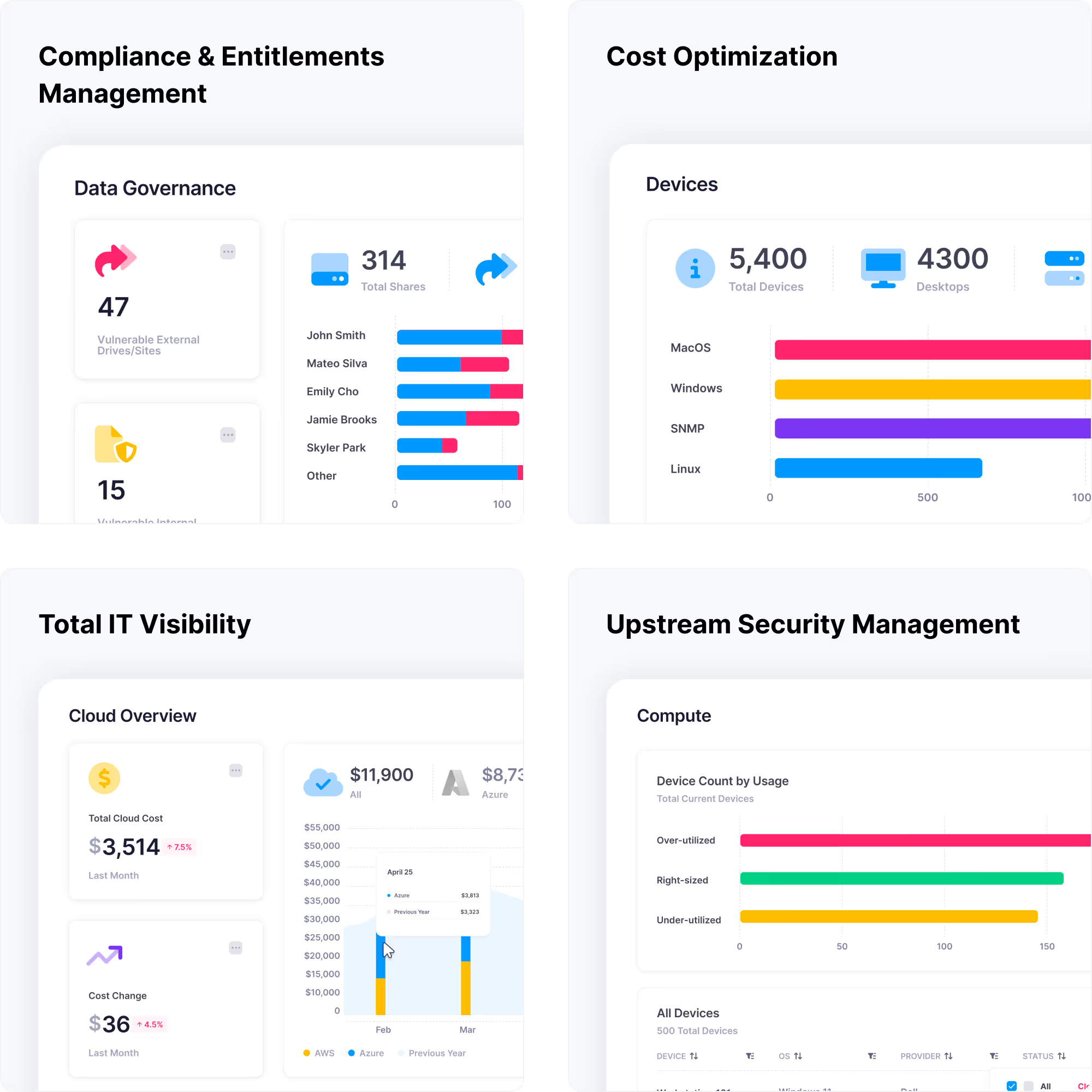
Complete IT asset visibility
One integrated toolset to discover, analyse and optimize assets across your hybrid IT environment.
Fast to deploy, easy to use
Agentless and agent based discovery methods deploy in less than 15 minutes without consultants, training or delays.
Priced for lean budgets
Transparent and affordable pricing ensures IT budget owners achieve up to 12x return on investment in Block 64.
Partner trusted, field tested.
Deployed in over 22,000 customer environments world-wide, trusted by top IT service providers.
Pioneers in IT asset management
We've invested 12+ years refining agentless discovery and usage monitoring —proven effective in every type of IT environment.
Secure by design
SOC 2 Type II certified and GDPR compliant, Block 64 only collects metadata, never reading or transmitting sensitive business data or PII.
Latest Blog Posts
Get your free scan and see where your IT is hiding
14 days free. 15 min set-up. No credit card required.